What is a VPN?
A VPN, or Virtual Private Network, is a service that creates a private and secure connection over a less secure network, such as the public internet. The primary goal of a VPN service is to ensure privacy and security for data transactions, making it harder for hackers, ISPs, or any third-party entities to see what you’re doing online or where you are located.
How does it work?
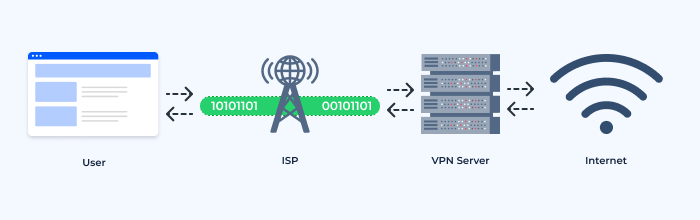
When you use a VPN service, your data is sent through encrypted tunnels to a VPN server, which then routes it to the internet. This process masks your IP address, making it appear as though you’re accessing the internet from the location of the VPN server rather than your actual location. Essentially, it acts as an intermediary between your device and the internet.
Benefits of Using a VPN Service:
| Privacy | Your online activities remain private as the VPN masks your IP address and encrypts your data, ensuring what you do online is known only to you. |
| Security | VPNs use strong encryption protocols to protect your data from hackers, cybercriminals, and even some government entities, making your online transactions and communications safer. |
| Geo-spoofing | By connecting to a server in a different country, you can access content that might be geo-restricted in your region. This is particularly useful for streaming services or accessing certain websites. |
| Bypass Censorship | In countries or networks where certain websites or services are banned, using a VPN allows you to bypass these restrictions. |
| Remote Access | For businesses, VPNs allow employees to securely access the company’s internal network from any location in the world. |
While a VPN service offers many benefits, it’s essential to choose a reliable provider. Not all VPNs are created equal, and some might log your data or provide inadequate security. Always research and select a trusted VPN service to ensure your online safety and privacy.
Why Should I Use a VPN Service?
In today’s digital age, where we spend a significant amount of time online, ensuring our digital privacy and security has become paramount. While the internet offers a world of information and connectivity at our fingertips, it also brings about risks and challenges. This is where VPN services come into play.
Here are some common reasons as to why you might use a VPN:
Secure your data
Every time you connect to the internet, you’re exposed to potential threats. Whether you’re checking your bank account, sending a confidential email, or simply browsing, your data can be intercepted and stolen. Using a VPN ensures that your data is encrypted, making it difficult for hackers, snoopers, or malicious entities to decipher the information, even if intercepted. This is especially crucial when using public Wi-Fi networks, which are often less secure and more susceptible to threats.
Work from home
With the rise of remote work, many employees need to access company resources from their homes. A VPN provides a secure channel to access corporate databases, emails, and other resources without the risk of exposing sensitive company data. It ensures that the data flow between the employee’s device and the company’s network remains private and shielded from potential cyber-attacks.
Access or stream regional content from anywhere
Ever been met with a “This content is not available in your region” message? Geographical restrictions can limit what you watch or access online. With a VPN, you can connect to a server in a different country and bypass these restrictions, allowing you to stream shows, movies, or access websites that might be blocked in your region.
Bypass censorship and surveillance
In some countries, internet usage is heavily monitored, and certain websites or platforms might be blocked due to government censorship. A VPN can mask your IP address, making it appear as though you’re browsing from a different location, allowing you to access restricted content and avoid government surveillance. This not only ensures your freedom to access information but also protects your privacy from state-led surveillance.
Prevent ISP and third-party tracking
Internet Service Providers (ISPs) often track and log your online activities. This data can be sold to advertisers or even handed over to authorities. A VPN hides your online actions from your ISP by routing your traffic through a secure server. Moreover, by masking your IP address, it makes it difficult for advertisers and other third parties to track your online behavior and target you with ads.
In conclusion, using a VPN service isn’t just for the tech-savvy or overly cautious. It’s a practical tool for anyone concerned about their digital privacy, security, and freedom. Whether you’re a business professional, a frequent traveler, or just an everyday internet user, there’s a VPN use-case that fits your online habits.
VPN Benefits
Using a Virtual Private Network (VPN) has become an essential tool for internet users worldwide due to the numerous advantages it offers. Here are some of the primary benefits of using a VPN:
- Enhanced Security: A VPN encrypts your online data, safeguarding it from hackers, cybercriminals, and potential eavesdroppers. Especially when connected to public Wi-Fi networks, a VPN acts as a protective shield for your sensitive data.
- Online Anonymity: By masking your IP address, a VPN allows you to browse the internet without revealing your identity. This ensures that your online activities are private and confidential.
- Geo-spoofing: Want to watch content that’s restricted in your country? VPNs can bypass geo-blocks, allowing you to access content from various countries by connecting to a server in the desired location.
- Bypassing Censorship: In countries with internet restrictions or heavy censorship, a VPN is a valuable tool to access blocked websites and platforms.
- Safer Online Transactions: For those who frequently conduct transactions or manage their finances online, a VPN offers an added layer of security, minimizing the risks associated with online banking.
- Reduced Online Tracking: Say goodbye to targeted ads. A VPN minimizes ad trackers, ensuring that advertisers find it challenging to target you based on your online behavior.
- Cost Savings: For frequent travelers, VPNs can help you get better deals on flights, hotels, and car rentals by masking your location.
How Does a VPN Work?
A VPN, at its core, is a complex technology that performs simple tasks: securing your online connection and masking your online identity. Let’s break down how it achieves this:
| Connection Establishment | When you activate your VPN software, it establishes a connection with a VPN server. This server can be located anywhere in the world, depending on your choice or the VPN’s automatic selection. |
| Data Encryption | Once connected, the VPN encrypts your internet data packets. This encryption ensures that anyone intercepting your data sees nothing but jumbled, unreadable text and numbers. |
| IP Address Masking | The VPN server you connect to assigns you a new IP address, effectively masking your real IP. This makes it appear as though you’re accessing the internet from the server’s location, not your actual location. |
| Data Transmission | As you browse the internet, your encrypted data is sent to the VPN server. The server then decrypts this data and sends it to its final destination on the internet, be it a website, online service, or another user. |
| Receiving Data | When data is sent back to you, the process is reversed. The VPN server encrypts the incoming data and sends it to you. Your VPN client then decrypts this data, allowing you to access it. |
| Ending the Session | Once you’re done with your online activities, you can disconnect from the VPN server. Your original IP address is restored, and your connection returns to its unencrypted state |
In essence, a VPN acts as a secure tunnel between your device and the internet. Everything you do online goes through this protected tunnel, ensuring your data’s confidentiality and integrity.
How do VPN servers operate?
VPN servers are specialized servers that handle incoming VPN traffic. They decrypt incoming data from users, send it to the internet, then encrypt the response before sending it back to the user. These servers are strategically located worldwide, allowing users to simulate being in different locations by connecting to them. High-quality VPN providers ensure their servers are maintained in secure data centers with high-speed connections.
How does VPN tunneling work?
VPN tunneling is a process in which data is securely transmitted over the internet in an encrypted tunnel. This tunnel ensures that the data remains confidential and cannot be easily intercepted or read by unauthorized parties. The creation of this tunnel involves encapsulating the data packet inside another packet before transmitting it through the public network.
OpenVPN
OpenVPN is an open-source VPN protocol known for its strong security and versatility. It uses SSL/TLS for key exchange and is capable of traversing network address translators (NATs) and firewalls.
SSTP
Secure Socket Tunneling Protocol (SSTP) is a proprietary Microsoft protocol. It’s integrated into Windows operating systems and uses SSL/TLS encryption, which ensures data confidentiality. Its main advantage is the ability to bypass most firewalls and proxy servers.
IKEv2 / IPSec
Internet Key Exchange version 2 (IKEv2) is combined with IPsec for a secure VPN connection. It’s known for its fast connection speeds, especially when reconnecting after an interruption. Developed by Microsoft and Cisco, it’s best suited for mobile devices.
L2TP / IPSec
Layer 2 Tunneling Protocol (L2TP) doesn’t offer encryption by itself. Instead, it’s often paired with IPsec for security. While slower than some other protocols due to double encapsulation, it’s considered to be quite secure.
PPTP
Point-to-Point Tunneling Protocol (PPTP) is one of the oldest VPN protocols. While it’s fast and built-in to many operating systems, it’s not considered the most secure option due to known vulnerabilities. It’s suitable for streaming but not for confidential data.
WireGuard
WireGuard is a newer VPN protocol praised for its lightweight design and impressive speeds. Built from the ground up for modern internet needs, it uses state-of-the-art cryptography and is gradually gaining popularity.
How a VPN protects your IP address
A VPN masks your IP address by replacing it with the IP address of the VPN server you’re connected to. This ensures that websites, online services, and potential trackers see the server’s IP address, not your actual one, thus preserving your online anonymity and protecting your location.
How secure is a VPN?
The security of a VPN depends on various factors: the protocol used, encryption strength, server configuration, and the VPN provider’s policies. Generally, reputable VPN services employ strong encryption and secure protocols, ensuring a high level of security. However, it’s essential to note that while a VPN significantly enhances online security, no tool can guarantee 100% security.
VPN encryption protocols
VPN encryption protocols determine how data is secured during transmission. The choice of protocol affects the speed, stability, and security of the VPN connection. Common protocols include OpenVPN, SSTP, IKEv2/IPSec, L2TP/IPSec, PPTP, and WireGuard. Each has its strengths and weaknesses, with some prioritizing speed and others prioritizing maximum security.
In choosing a protocol, users must weigh their specific needs against the benefits and limitations of each protocol.
Types of VPN Connections
As the importance of online privacy and security grows, various types of VPN (Virtual Private Network) connections have been developed to cater to different needs. Each type serves a specific purpose, offering unique advantages depending on the user’s requirements.
Personal VPN
A Personal VPN, often referred to as a consumer VPN, is primarily designed for individual users. Its main purpose is to provide privacy, security, and access to geo-restricted content. When using a Personal VPN:
- Your online activities are encrypted, preventing unwanted surveillance or data theft.
- Your real IP address is hidden, ensuring online anonymity.
- You can access content that may be restricted in certain regions.
Remote access VPN (also known as client-to-site VPN)
Remote access VPNs are essential for businesses and organizations, allowing employees and members to securely access a private network from remote locations. Features include:
- Users connect via a VPN client installed on their device.
- It offers a secure and encrypted connection to the organization’s private network.
- Essential for remote workers, ensuring they can access company resources without compromising security.
Site-to-site VPN
Site-to-site VPNs are used to connect entire networks to each other. For instance, a business may use a site-to-site VPN to connect its main office network with networks in its satellite offices.
Intranet
If a company has multiple remote locations and wishes to join them into a single private network, they can establish an intranet VPN. This setup allows different branches of the same company to share information securely over the internet.
Extranet
An extranet VPN connects different companies’ networks, allowing them to share data securely. For instance, a company might connect with its supplier’s network to facilitate easier communication and data sharing while keeping unauthorized parties out.
Mobile VPN
Mobile VPNs are designed for the specific challenges posed by mobile devices and their connection to various networks. Unlike traditional VPNs, a mobile VPN allows for a seamless transition between networks (e.g., from Wi-Fi to cellular) without dropping the connection. This type is ideal for:
- Professionals who are constantly on the move.
- Users in regions with unstable internet connections.
- Ensuring a consistent and secure connection regardless of the network’s reliability or security.
In conclusion, the type of VPN connection one should opt for largely depends on the specific needs, whether it’s individual privacy, business data sharing, or maintaining a constant secure connection on mobile devices.
What Does a Good VPN Do?
In an age of growing cyber threats and increasing awareness of online privacy, choosing a reliable VPN (Virtual Private Network) has become paramount. A good VPN offers more than just encrypted browsing; it provides a comprehensive suite of features designed to protect user data, ensure privacy, and enhance online experiences. Here’s what you should expect from a top-tier VPN service:
Strong protocols
Protocols determine how your data is transmitted and encrypted. A reliable VPN should support multiple protocols, such as OpenVPN, SSTP, IKEv2/IPSec, and more. The flexibility to switch between protocols allows users to balance between speed and security according to their needs.
IP address protection
A fundamental function of a VPN is to mask your real IP address, ensuring your online activities remain anonymous. A good VPN provides IP leak protection, ensuring that your real IP address is never unintentionally exposed.
A range of servers across many locations
Having access to a broad network of servers in various countries and regions allows users to:
- Bypass geo-restrictions.
- Access content from different countries.
- Ensure a fast connection by choosing a server close to their location.
Zero-log policy
One of the primary reasons people use VPNs is for increased privacy. A strict zero-log policy ensures that the VPN provider does not keep records of your online activities. This means even if they’re approached by authorities, they have no user data to hand over.
Kill switch
A kill switch is a security feature that automatically disconnects your device from the internet if the VPN connection drops unexpectedly. This ensures that your data isn’t accidentally transmitted over an unsecured connection.
Mobile compatibility
With the increasing use of smartphones for internet access, a top VPN should offer dedicated apps for various mobile platforms, ensuring secure browsing on the go.
Options for authentication
Multiple authentication options, like multi-factor authentication, add an extra layer of security. This ensures that even if someone gains access to your password, they can’t access your VPN without the second authentication factor.
Customer support
Strong customer support is essential for any service. A good VPN should offer 24/7 customer support through various channels, such as live chat, email, and phone, ensuring users get timely assistance when needed.
Premium pricing
While there are free VPNs available, they often come with limitations and potential security risks. A good VPN typically comes at a premium price, which is justified by the high-quality servers, robust security features, and continuous development and support. It’s essential to ensure you’re getting value for your money by considering the features offered against the price.
In essence, when choosing a VPN, don’t just focus on one feature. A comprehensive approach, considering all the aspects mentioned above, will ensure a secure, private, and seamless online experience.H2 What should I look for when choosing a VPN?
Setting Up a VPN Connection
Setting up a VPN connection is straightforward, but the exact steps can vary based on the device, operating system, and VPN provider. Here’s a generalized guide to help you set up a VPN:
- Choose a Reliable VPN Service: Before anything else, select a reputable VPN provider that matches your requirements in terms of security, speed, and server locations.
- Sign Up & Download: Once you’ve chosen a provider, sign up for their service and download the appropriate VPN client or app for your device.
- Installation: Install the VPN client or app, much like you would with any other software or app.
- Login: Open the VPN client and log in using the credentials you provided during sign-up.
- Select a Server: Most VPN apps will let you choose a server location. Pick one that’s suitable for your needs. For instance, if you’re looking to access content from a particular country, select a server from that location.
- Connect: Hit the ‘Connect’ button. Once connected, your data will be encrypted, and your online activities will be masked behind the VPN server’s IP address.
- Ensure Security: Check for any potential IP or DNS leaks to ensure your connection is secure. Some websites provide this service for free.
- Disconnecting: When you’re done, you can disconnect from the VPN server using the app.
Remember to always keep your VPN client updated to the latest version to ensure optimal security and performance.
How Do VPNs Help with Identity Theft?
Identity theft involves stealing personal information to commit fraud, and it’s a growing concern in today’s digital age. A VPN can play a crucial role in shielding you from potential identity theft in the following ways:
| Encrypted Data Transmission | VPNs encrypt your data, making it unreadable to hackers, cybercriminals, and even ISPs. This ensures that sensitive information, such as login details or financial transactions, is secure during transmission. |
| Masking IP Address | By hiding your actual IP address, VPNs make it harder for cybercriminals to track your online activities and gather data about you. |
| Safe Online Transactions | When making online payments or accessing banking details on public Wi-Fi, a VPN provides an added layer of security against potential eavesdroppers. |
| Protection from Phishing Websites | Some VPN services offer malware and phishing protection, preventing users from accessing malicious websites that can steal personal information. |
| Blocking Tracking & Profiling | VPNs can prevent various tracking methods, such as cookies or digital fingerprinting, used by websites and advertisers. This reduces the chances of targeted phishing attacks based on your online behavior. |
| Secure Remote Access | For businesses, VPNs ensure that employees can access company resources remotely without the risk of exposing sensitive data. |
While VPNs provide a significant level of protection against potential identity theft, they are just one tool in the arsenal. It’s crucial also to follow best practices like using strong, unique passwords, enabling multi-factor authentication, being cautious of suspicious emails or links, and keeping software updated.
Find Out Who is Hosting Any Website with Website Hosting Checker
SiteChecker’s Website Hosting Checker tool is an exceptionally user-friendly service that provides instant insights into any site’s hosting provider. It’s an invaluable resource for webmasters and competitive analysts who want to understand the hosting landscape of their own or competitor’s websites. With a simple URL entry, the tool quickly reveals the host, helping to assess the speed, reliability, and credibility of the hosting services used.
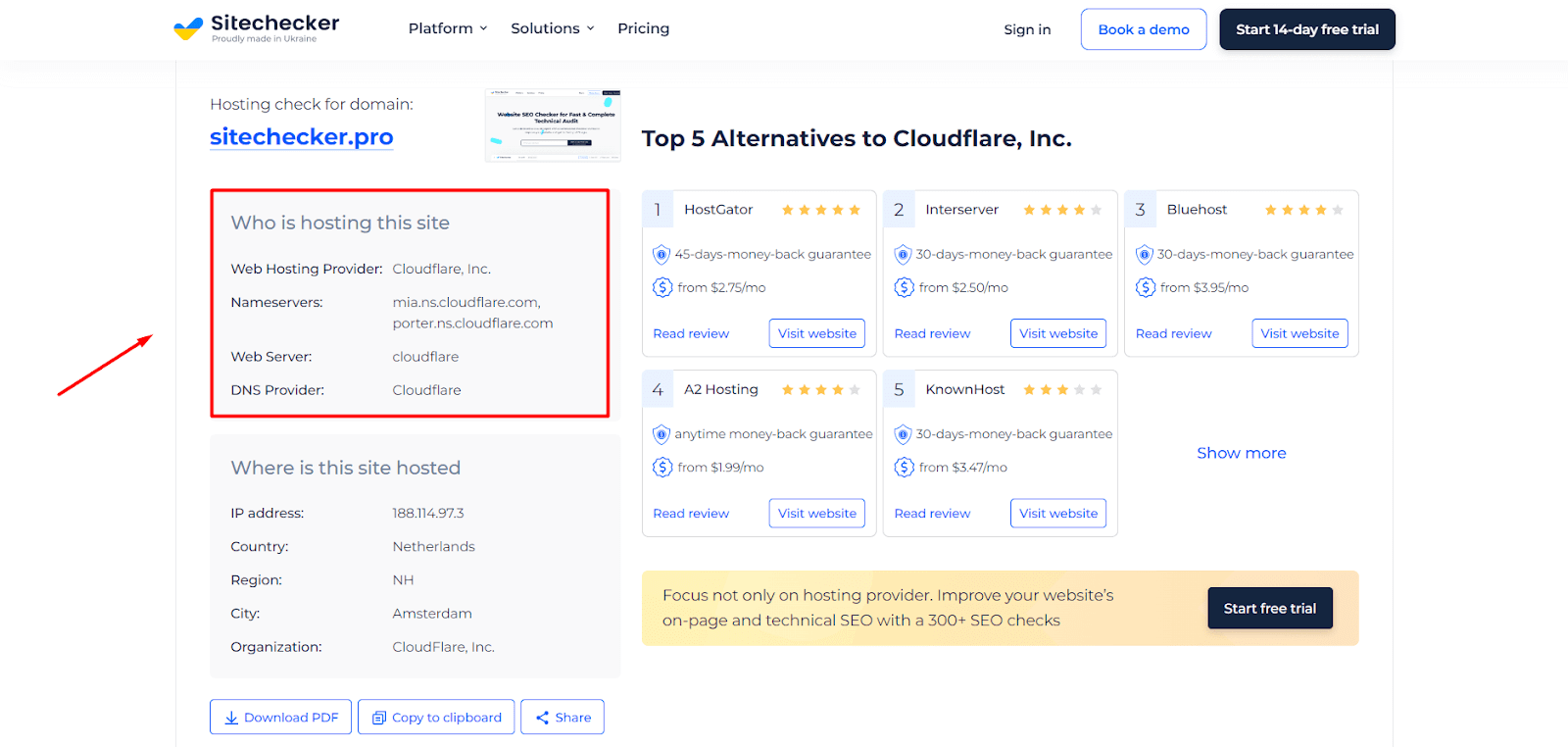
Besides identifying the host, the tool offers a deeper dive into the hosting details, including the server’s IP address and geographical location. It also lists other domains hosted by the same server, which can be crucial for SEO professionals looking to avoid ‘bad neighborhoods’ or for those researching hosting options. This comprehensive approach makes the Website Hosting Checker a critical tool for anyone serious about web presence and performance.
Reveal the Hosting Behind Any Website!
Our Website Hosting Checker delivers the intel you need with just one click.
Conclusion
In today’s digital age, where online privacy and security have become paramount, VPNs serve as a critical tool in our daily digital interactions. They not only offer encrypted connections, ensuring our personal data remains out of the reach of cybercriminals, but also enable us to access a world of content unrestricted by geographical boundaries. Beyond just bypassing geo-restrictions, VPNs stand as a shield against identity theft, unwanted surveillance, and potential data breaches. As our dependence on the internet continues to grow, understanding and utilizing VPNs becomes not just a matter of convenience but of safety. So, whether you’re a casual browser, a remote worker, or just someone keen on preserving their digital footprint, investing in a reliable VPN is a step forward in a more secure online journey.